In order to compare our new method with the decomposed method, we
summarize the decomposed method discussed
in [8, 9]. Assume that Server k serves n+1
connections. Similarly, let ![]() and
and ![]() be the input and output traffic functions of Connection i, and
be the input and output traffic functions of Connection i, and
![]() and
and
![]() be the constraint functions of input and output
traffic of Connection i, for
be the constraint functions of input and output
traffic of Connection i, for ![]() . Furthermore, we denote
. Furthermore, we denote
![]() as the local delay bound suffered by all input traffic at server
k.
as the local delay bound suffered by all input traffic at server
k.
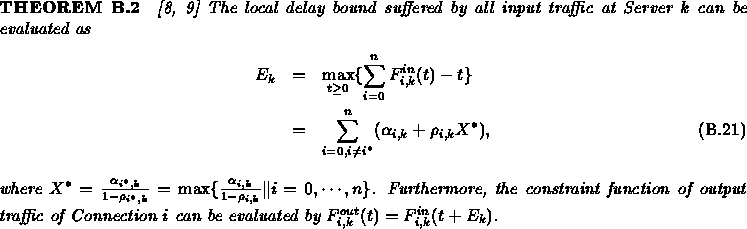
Now we use the decomposed method to study the example presented in Section 4.
For this, we assign the middle output port of the k-th switch as the
k-th server in the network. We also denote ![]() as the local delay
bound suffered by all traffic at the k-th server. Using the above
theorem, we have that
as the local delay
bound suffered by all traffic at the k-th server. Using the above
theorem, we have that
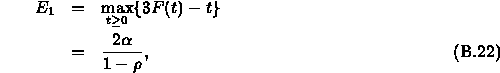
and
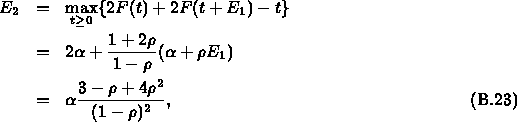
and for k>2
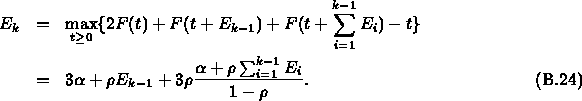
Therefore, the end-to-end delay bound ![]() for Connection 0 is
computed by Algorithm Decomposed as
for Connection 0 is
computed by Algorithm Decomposed as
![]()